Modeling a simple example
To start your model, first, create an empty ThreatGet diagram, as shown in the section Creating a diagram. The ThreatGet Toolbox is automatically selected after pressing Create Pattern. The standard ThreatGet toolbox has elements of different categories as well as connections and boundaries.
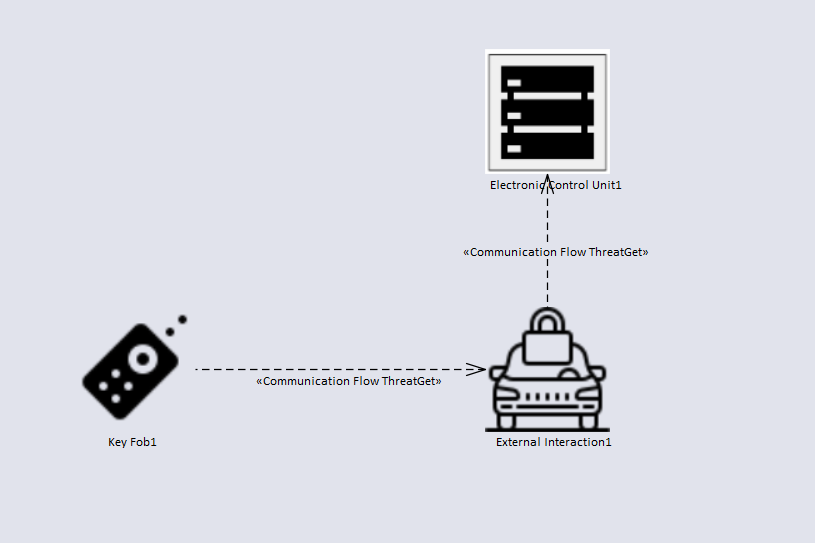
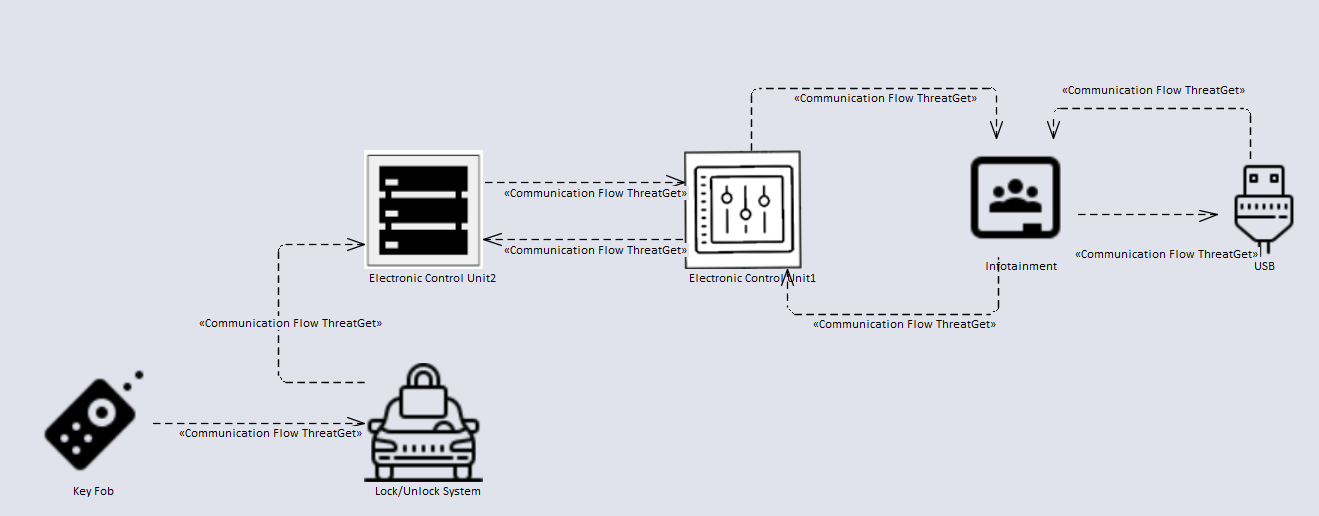
The model represents a realistic example. It is the communication between a key fob and a car. The purpose of communication is to lock and unlock the vehicle. The key fob communicates via an antenna with a lock / unlock control unit. The signal is received via the antenna and passed on to the central control unit. The received signal is processed, then the feedback is sent to the users (e.g., the sight lights go on and off). The central control unit is connected to the infotainment system. The infotainment contains an integrated USB port. Both ECU's are communicating internally.
We need the following elements for modeling:
- Key Fob from the Key Fob category
- Vehicle from the External Interaction category
- High-performance ECU from Electronic Control Unit category
- Communication ECU from the Electronic Control Unit category
- Infotainment from the Electronic Control Unit category
- USB from the Interface category
Note: All connections are selected as Communication Flow from the Communication Flow category to simplify modeling.
Create the key fob, vehicle, and high-performance ECU from the ThreatGet ToolBox by drag and drop. Create the connections by selecting Communication Flow from the Toolbox. Then click on the source element and keep the mouse button pressed and release the button over the target element.
Now double-click on an element to access the element properties. In our case, we change the properties of the vehicle. In the first step, we change the name to lock/unlock antenna.
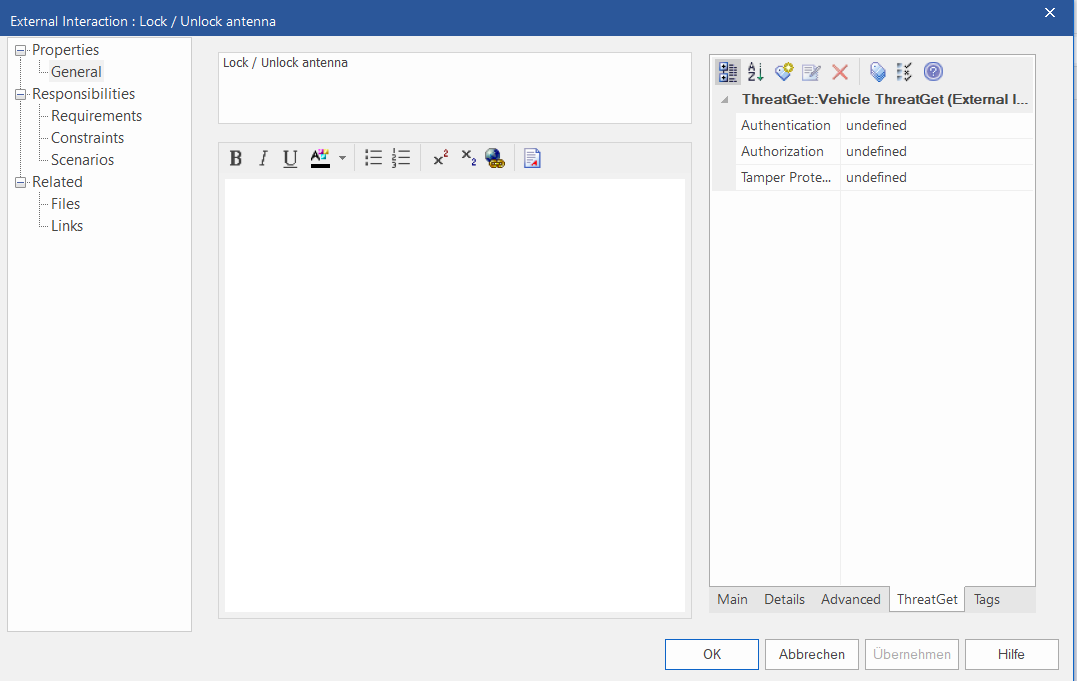
The properties also include ThreatGet Tagged Values. These are properties that were created by the Server Administrator.
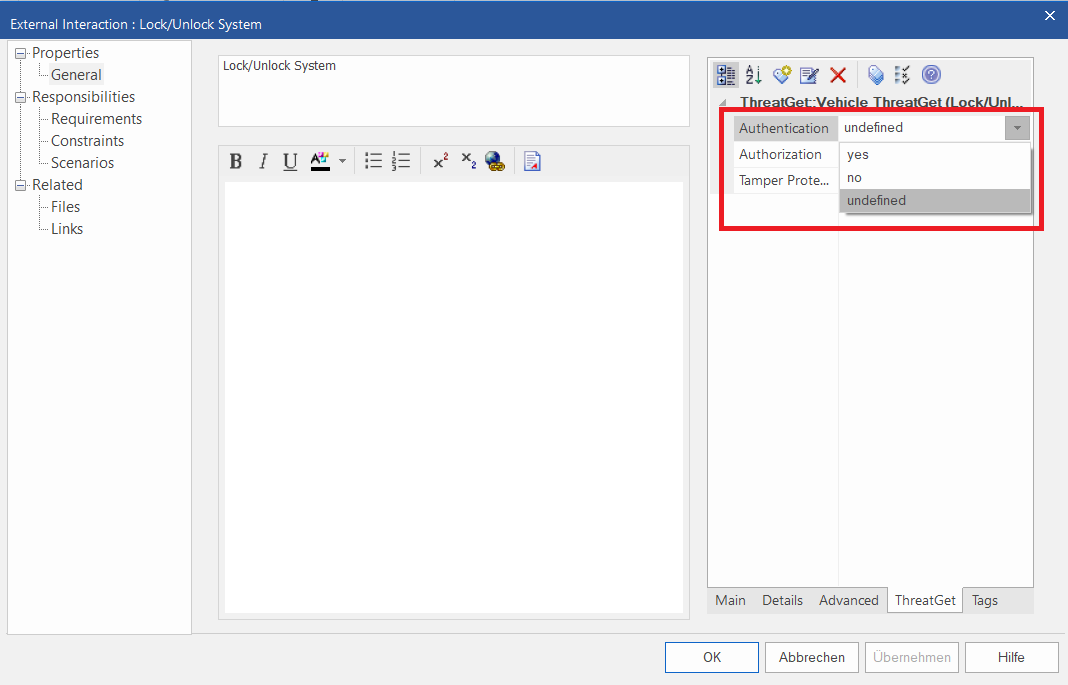
It is possible to change the values. Here you can always change one of the values from the dropdown menu.
We now create the elements mentioned above, step by step, and then connect them with the connections. Your model should look like the diagram below.
We are now ready to perform a threat analysis on this example.